Russian cyber attacks on the US electrical grid have mostly been about network access. But with rising tensions, could attacks escalate?
The US Grid System
With rapid expansion of automation and computer-controlled electrical grid systems, the United States must face the reality that cyber threats to the critical infrastructure of energy production are concurrently advancing at an equivalent rate. The US electrical grid system is the world’s largest interconnected machine made of 200,000 miles of high voltage transmission lines and over 5.5 million miles of local distribution lines to service over 3,000 different utility providers among the Eastern, Western, and Texas power sectors. As the needs for electricity grow, energy providers are forced to utilize automated control systems in order to keep up with the complexity of transmission and consumer delivery. The expanded use of automated and computer-controlled systems have provided the opportunity to increase affordability and reliability by cutting out the human component, yet leave a significant vulnerability for threat actors to be able to manipulate power distribution remotely.
ICS cybersecurity attack expectations
Russian Interference
A recent report released by the Department of Homeland Security (DHS) in March 2018 details the cyber intrusion techniques that Russian government cyber actors utilized to infiltrate the Western energy and critical manufacturing sectors. The report characterizes the incidents as network reconnaissance and information collection on U.S. Industrial Control Systems (ICS). Threat actors were able to gain access to the network through a series of spear-phishing emails and undetectable malware downloads to obtain employee credentials and establish administrator accounts in order to re-enter the system at will.
Once in the system, the actors were able to move freely and gather information on the ICS system defenses through screenshots and remote downloads. Though the actors were contained to a limited amount of information before being removed, the DHS in conjunction with the FBI want to emphasize the growing need for network security of critical infrastructure systems, and educate employees on the growing number of intrusion techniques used by threat actors.
Threat Categorization
Cyber threats are categorized into a two-stage process known as the ICS Cyber Kill Chain Model. Stage I attacks are strictly network access and systems intrusion that focus on access and ability to move freely within the operating system. In the report previously mentioned the DHS categorized the most recent infiltration attempts as stage I attacks. Successful stage II attacks are more severe in nature and can result in potential loss of electricity generation or transmission for long periods of time.
These types of attacks committed by Russian actors could be seen in the 2015 attack on the Ukrainian electrical system, in which 235,000 people lost power due to a carefully orchestrated interference attempt. Dragos Inc., a U.S. cybersecurity firm, determined that the malware, CRASHOVERRIDE, was able to breach the ICS control system and temporarily shut down physical transmission, leading to hours of blackout. This attack was only the second recorded successful stage II attack to disrupt a physical system in the energy sector in the world.
While the Russian actors only gathered information and access to control systems in the most recent U.S. attack, without proper cyber intrusion detection the United States is potentially vulnerable to future access and more severe ICS attacks similar to the incident in Ukraine. In a recent Scientific American interview, Robert Lee, CEO of Dragos Inc., stressed the distinction between the attacks the United States incurred and the Ukrainian disruptions in 2015. He mentioned that the United States sees a large amount of stage I activity, where information gathering and positioning is taking place, yet he does not see an advancement or “pivot” to a stage II attack without a significant conflict scenario.
Motives and Future Consideration
To illustrate Russian actors’ motives the Energy Department released a graphic as part of a report on cyber threats and vulnerabilities in the electric sector:
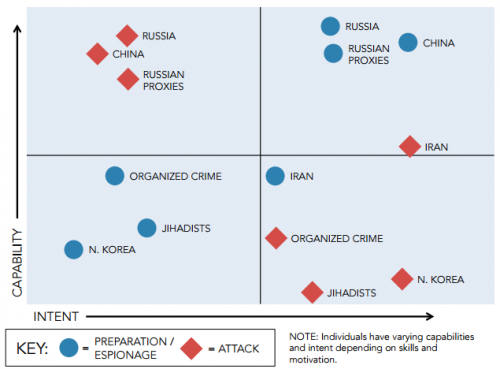
Figure 3, on pg. 21 of Cyber Threat and Vulnerability Analysis of the US Electric Sector
The threat actors within the matrix of capability and intent vary in their desired impact on the U.S. energy sector. While this report was released in 2016, the assessment of Russian threat actors still holds true that there have been efforts to infiltrate and move within operating systems, but there has not been successful efforts to commit a stage II attack in the United States thus far.
The looming question is how the changing landscape of U.S.-Russia relations will affect the types of attacks seen on the energy grid. All signs lead to a growing amount of stage I infiltration attempts by various threat actors, yet there has not been momentum to pivot into stage II activity. With tensions growing larger as the United States sanctions Russia over increasingly aggressive action including interference in the 2016 election, the U.S.-Russia relationship is elevating into a potential conflict scenario.
In anticipation of future attacks to the energy sector, there has been significant traction in the conversation surrounding cybersecurity of the nation’s power grid to increase defense systems. Rick Perry, Secretary of Energy, stressed the importance of increasing protections to energy infrastructure security by establishing the Office of Cybersecurity, Energy Security, and Emergency Response. The statement released by the Department of Energy also includes the request for $96 million in funding for the office that was included in the President’s FY19 budget. The Office aims to provide support to the energy industry by bolstering energy providers’ defense practices in order to ensure reliable energy transmission to consumers and deter cyber attacks. Overall, if provocations advance and the tit-for-tat sanctioning escalates, the United States could see a shift in Russian intent from espionage and information gathering to physical threats and disruption campaigns.
Photo by Daniel (vernetzt) via Flickr.
Taylor Howard is a Master in Public Policy student in his second year at the McCourt School of Public Policy, where he is focusing on the nexus of energy and national security policy. He is from the Atlanta area, and received a Bachelor’s degree in Political Science and Psychology from Auburn University in 2017.
